Root of Trust
- Just how do you recognize if a jeopardized OS was booted at runtime?
- Can you rely on that your certifications are kept securely?
- Has the kernel or various other system software been compromised?
- What are the guarantees called for? High-security enterprise companions need near-total ability to audit the software and also manage interfacing with their systems. Device users should have the authority to deny authorization to utilize their device features and information. Each individual, partner, as well as integrated system has its own needs, a number of which are assured in large part via the Roots of Trust.
- How can components contribute to more complex assurances? A Trusted Boot procedure enables the reliable transfer of control from the bootloader to the Android structure. This reliable transfer of control plays a crucial function in the IT admin's capacity to investigate apps running on the tool.
- How can we make these components, their assurances, and their usage more robust? Each Trusted Application on a Infiniti ultimately has a Root of Trust. These Trusted Applications incorporate capability such as tool identity, key monitoring, and also remote attestation of hardware health.
INFINITI IN HIGH THREAT ENVIRONMENTS
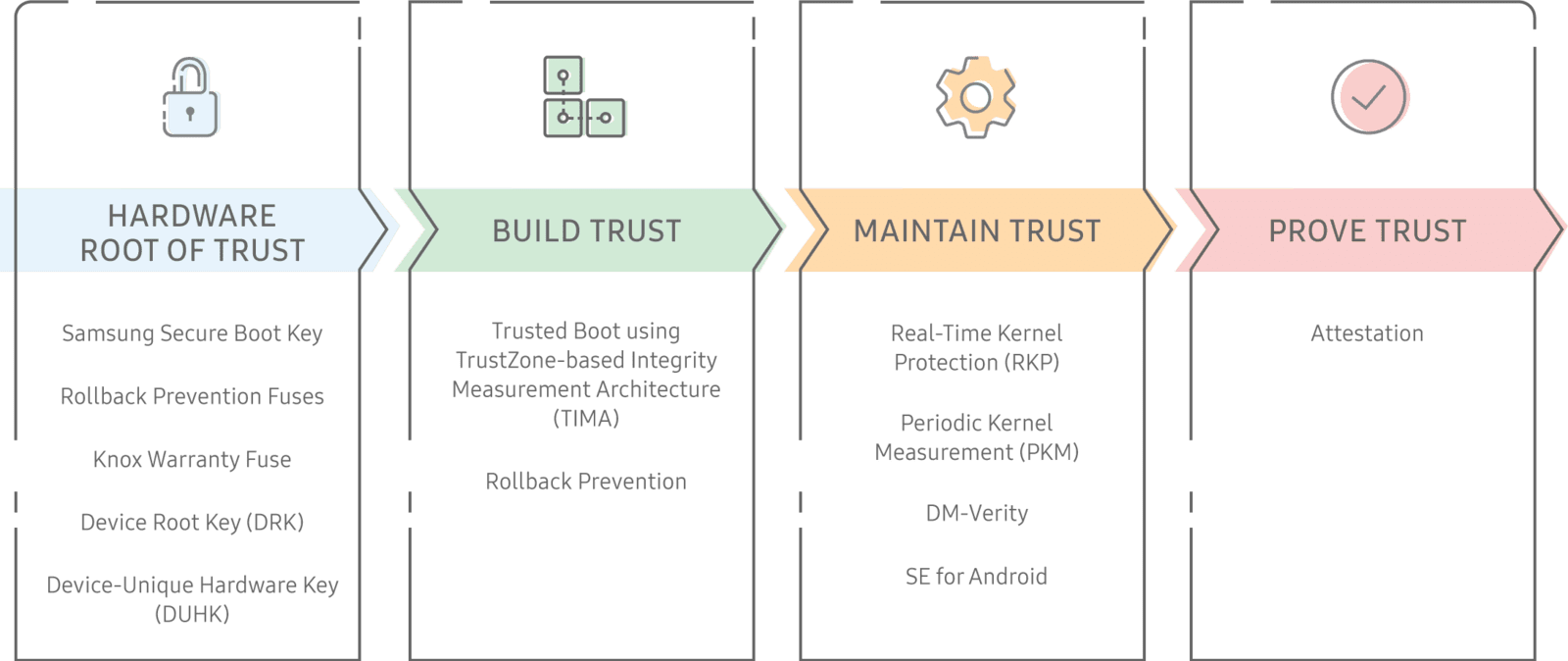
- Establishes a hardware-backed Root of Trust, on which various other elements depend.
- Develops depend on during boot, through functions like Trusted Boot.
- Maintains count on while the tool is in use, with features like Real-Time Kernel Protection.
- Verifies its trustworthiness on demand, through Device Health Attestation.
JUST HOW THE ROOT OF TRUST WORKS
- Omerta Infiniti protection begins in the factory - months prior to individuals even powering on their devices - when a Device-Unique Hardware Key (DUHK) is created on the devices using a hardware random number generator.
- Next, the DUHK generates and also encrypts the Device Root Key (DRK) as well as Samsung Attestation Key (SAK).
- Upon device start up, Infiniti makes use of the Samsung Secure Boot Key (SSBK) to check all software parts. One of the components is the TrustZone Secure World, a zone for safe code & data execution. Only secure software applications components running within the TrustZone Secure World can access these.
- The software does a check on each Knox Platform attribute before allowing it to run. Considering that this chain of safety and security checks begins with the very initial hardware check, each feature is secured by hardware Root of Trust. No matter which link in the chain an attacker targets, one of the protection checks discovers it.
SAFE AND SECURE HARDWARE
- Bootloader ROM — The Primary Bootloader (PBL) The PBL is trusted to measure and verify the boot chain. The device also runs the PBL from ROM at boot, and the PBL starts the Secure and Trusted Boot procedures.
- ARM TrustZone Secure World -- The Secure world is the setting in which very sensitive software runs. The ARM TrustZone makes sure memory and hardware marked secure (e.g a fingerprint reader) can only be accessed in the Secure World. The majority of the system, including the kernel, middleware, and applications, run in the Normal World. The Secure World software, on the other hand, is much more privileged, & can access both Secure and Normal World resources.
- Knox Vault-- The Knox Vault is an independent, tamper-proof, protected subsystem with its very own processor, memory, and an interface with specialized non-volatile storage space. The Knox Vault stores delicate information such as cryptographic secrets and also authentication data. Even if the main application processor that runs Android is jeopardized, the Knox Vault secures keys and defend against equipment attacks such as probing and also mistake shot.
hARDWARE kEYS
- Device-Unique Hardware Key (DUHK)-- Samsung incorporates the DUHK, a device-unique symmetric key, in the device equipment throughout the initial manufacturing of the device. The DUHK binds information-- for instance, tool wellness attestation information-- to a certain gadget and also comes only by a hardware cryptography component and also not straight exposed to any kind of gadget software application. However, software program can ask for that the DUHK secure as well as decrypt data. This DUHK encrypted information is bound to the device, as well as therefore can not be decrypted on any other gadget.
- Device Root Key (DRK)-- The DRK is a device-unique, crooked RSA vital set that is signed by Samsung's origin trick via an X. 509 certificate. This certificate proves that Samsung produced the DRK. The DRK is produced at manufacture in the Samsung manufacturing facility and is saved on the device encrypted by the DUHK, thus binding it to the gadget. The DRK is just easily accessible from within the TrustZone Secure world as well as is protected by the DUHK. The DRK is a fundamental part of the Root of Trust, as it acquires various other signing secrets. Since the DRK is device-unique, it can tie information to a tool via cryptographic signatures. Authorizing tricks are derived from the DRK and made use of to authorize data.
- Samsung Secure Boot Key (SSBK)-- The SSBK is a crooked essential set made use of to authorize Samsung-approved boot executables.The private part of the SSBK is used by Samsung to authorize secondary and app bootloaders.The public part of the SSBK is kept in the hardware's one-time programmable merges at manufacture in the Samsung factory. The Secure Boot process utilizes this public trick to verify whether each boot component it tons is accepted.
- Samsung Attestation Key (SAK)-- The SAK is likewise a device-unique, crooked vital pair that is authorized by Samsung's origin trick. This authorized vital pair confirms that the SAK was generated by Samsung. The SAK is made use of to authorize the Attestation blob that shows if the tool remains in a relied on state. The trademark verifies that Attestation data originated from the TrustZone Secure world on a Samsung gadget. Unlike the DRK, the SAK is a set of ECDSA secrets. ECDSA is a more recent asymmetric algorithm, similar to RSA yet smaller sized as well as much faster for the exact same strength.
hARDWARE fUSES
Samsung Knox safety is built in layers, from low-level capabilities in the hardware to Android itself. One of the vital low-level features are the hardware integrates, which give a Root of Trust based in hardware. Samsung Root of Trust elements are developed as single integrates, making an irreversible document of information such as encryption tricks, Rollback Prevention, and also the Knox Warranty.
ROLLBACK PREVENTION (RP) FUSES
KNOX WARRANTY FUSE
- an unsigned kernel is filled
- an essential protection attribute like SELinux is impaired